Characteristics and Security Features of Cloud Environment

The spread of COVID-19 has raised interest in cloud computing, and companies are stepping up their migration to cloud for several reasons, including changes in their ways of work due to the pandemic or for vitalizing business. As such, they are paying greater attention to cloud migration, a process of moving their business elements to a cloud computing environment.
A majority of companies have already shifted their day-to-day computing business from on premises to cloud, and most global IT services are now cloud-based. As a result, cloud migration and cloud-based system implementations have become major business areas of Samsung SDS in recent years.
I have participated in a project to migrate the legacy systems built on Amazon Web Service (AWS) to Samsung SDS private cloud and the one to newly build clients’ AI systems on Samsung SDS private cloud. By going through these projects, I realized once again that cloud is the leading trend in the IT industry.
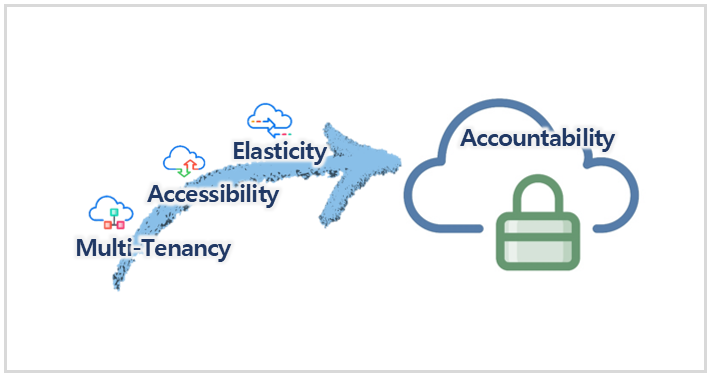
Today, let’s learn about the key characteristics of the cloud -- multi-tenancy, accessibility, and elasticity -- and its security feature called accountability.
# Multi-Tenancy: Sharing Borrowed IT Resources
Multi-tenancy means several tenants living in one house. Imagine a four-story house, with tenants residing on the first three floors and the owner living on the top floor. These multiple tenants pay monthly rent and use the facilities without having to worry about maintenance. However, they can change the interior design of their own space as they please. Cloud services are similar to this. Cloud service providers like AWS, MS Azure, and Samsung SDS logically divide and separate physical resources using virtualization technology and lend them to multiple cloud users.
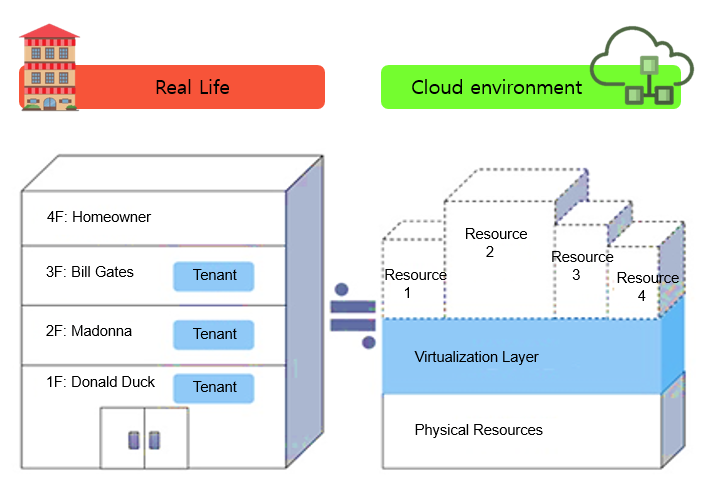
As you can see from the above image, Resources 1, 2 and 3 are rented to cloud users. Of course, common cloud areas created by cloud service providers -- cloud management portals, power management of physical resources, and server rack management (SRM) -- are directly managed by the service providers, whereas the internal setup like creating access accounts, installing software, or changing OS setups for the rented resources are up to cloud users, just like tenants changing the interior design of their rented space. However, sharing physical resources can lead to data breach issues due to security defects.
# Accessibility: Access Cloud Anytime, Anywhere
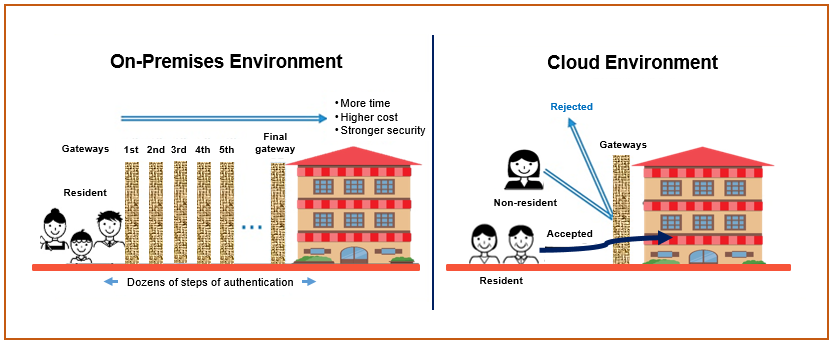
The second characteristic of cloud is accessibility. It means users can easily access the cloud resource via Internet. In the existing on-premises environment, every route to IT resources has gateways with several security systems, like firewalls, to control (authenticate/authorize) all access to IT resources. However, cloud users can immediately adjust security levels by simply clicking buttons through an access control list (ACL) and firewalls that are provided as security services. Thanks to this, users can conveniently access cloud resources regardless of device types, anywhere, anytime.
However, users should exercise extra caution when granting and disabling access, as well as with authentication and authorization systems because a cloud environment can be used regardless of time and space.
# Elasticity: Ease of Increasing or Reducing Resources
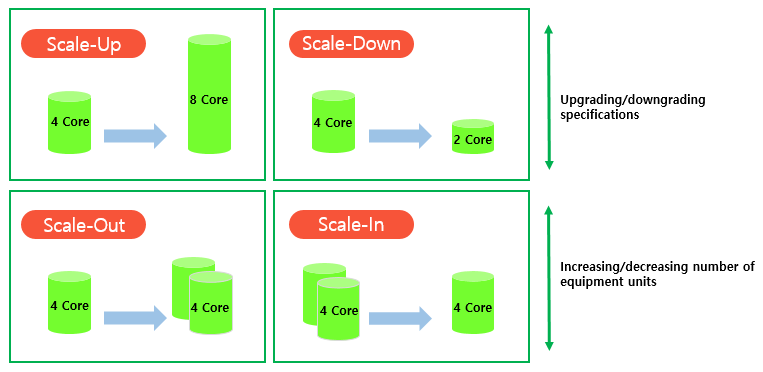
The last characteristic of cloud is elasticity. It is the ability to increase, reduce, add, or remove resources. In other words, a cloud environment allows easy resource adjustments, such as ‘scale-up’ (upgrading specifications), ‘scale-down’ (downgrading specifications), ‘scale-out’ (adding identical resources), or ‘scale-in’ (removing redundant resources).
# Accountability: Holding Users Responsible for Their Behavior on Cloud
Until now we learned about key characteristics of a cloud environment – multi-tenancy, accessibility, and elasticity – and now let’s go over security threats. Cloud resources change dynamically and resources can be added or removed by misuse of authorization or can be exposed to various security threats, such as cloud resource attacks, intentional breach of sensitive data, or unauthorized access.
Therefore, it is crucial to construct a security architecture using cloud security services to ensure accountability. It refers to recording the behaviors of identified users who access cloud and utilize resources and holding them responsible for their behaviors.
Cloud accountability requires identification, authentication, and authorization prior to using resources, logging and monitoring their use, and an audit of the activity history after resources are used.
A cloud environment is similar to an on-premises environment in certain aspects, but clouds have distinct characteristics and unique security features as explained above. I hope you find this article useful for understanding what is unique about cloud, including the specificity of its security features.
Related Articles
-
Samsung SDS Named in Gartner Magic Quadrant for Data Center Outsourcing and Hybrid Infrastructure Managed Services, Global
-
Samsung SDS Cloud Security Services Acknowledged as a Major Player in the IDC Report
-
[Technology Toolkit]
No More Short of GPU!
-
Characteristics and Security Features of Cloud Environment
-
Samsung SDS Positioned in Gartner Magic Quadrants for Data Center Outsourcing & Hybrid Infrastructure Managed Services in Asia Pacific and Europe
-
Samsung SDS positioned in 2019 Gartner Magic Quadrant for Cloud Managed Service
No More Short of GPU!