
Background
For problems associated with research, business and society in general, the answers can be found by gathering and utilizing scattered data. Unfortunately, the entire world is currently struggling with their fight against the novel COVID-19. What’s alarming is that pandemics like COVID-19 will become more widespread and frequent in the future. A 3-step management process (test-trace-quarantine) is necessary to effectively deal with outbreaks such as this but it nevertheless entails its own challenges, especially the second step – trace – where there is an issue of personal information leakage and difficulty in identifying potentially infected persons who crossed paths with an infected person. Here we would like to introduce a method that will help you to overcome these shortcomings - a method that will enable you to use the available data to trace potentially infected persons in real time whilst protecting their personal information.Z
What is the problem?
When an individual has tested positive for COVID-19, KCDC (Korea Centers for Disease Control and Prevention) quickly retraces his/her recent movements and makes the information known to everyone in the country. The authority takes a cautious measure in keeping sensitive information including name and birthday of an infected person private when releasing his/her movement information to the public. However, there is still a risk of personal information leakage if someone purposefully uses other additional information available to identify an infected person. Moreover, it is nearly impossible to identify persons who were in the same path with an infected person in real time.
How can we solve the problem?
Homomorphic encryption is a new encryption technology that allows computation on encrypted data. You can use this technology to identify persons who were in the same paths with an infected person in real time whilst protecting personal information of the infected person as shown below.
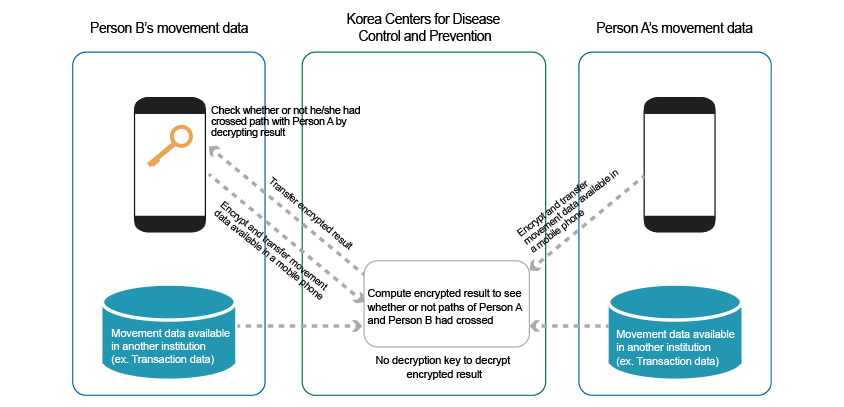 [Diagram 1] Computation of encrypted movement data of COVID-19 carrier using homomorphic encryption technology
[Diagram 1] Computation of encrypted movement data of COVID-19 carrier using homomorphic encryption technology
Let’s assume that ‘Person B’ wants to see if he/she had crossed the same path with ‘Person A’ – the COVID-19 carrier. This is where homomorphic encryption technology comes into play. Person B encrypts his/her movement data and sends it to KCDC who then computes/compares the encrypted data from both Person B and Person A, and sends back the result to Person B.
The fact is KCDC does not have a decryption key to decrypt encrypted data and as a result is not capable of identifying movements of not only Person B but Person A as well. Instead, what they do is they compute the encrypted movement data of these two individuals using the homomorphic encryption technology to see whether or not their paths had crossed (homomorphic encryption technology allows computation of data while it’s encrypted). The ‘result is then encrypted and sent to Person B, the only one with a decryption key to decrypt corresponding result. In short, with this technology, Person B can learn whether or not he/she had crossed the same path with Person A in real time whilst protecting not only his/her own private information but that of Person A.
Of course there are circumstances that require KCDC to be aware of and use the ‘result’ in their dealing with COVID-19. If movement paths of Person B and Person A overlap, Person B can probably make the information known to KCDC. But as seen in [Diagram 2], instead of relying on Person B to share the information, the trusted authorities can set up a separate institution to be in charge of key escrow, i.e. management decryption key and have them receive/decrypt encrypted result only and send the information to KCDC. This allows KCDC to only see the information that requires a next step and thereby minimize any unnecessary leakage of personal information.
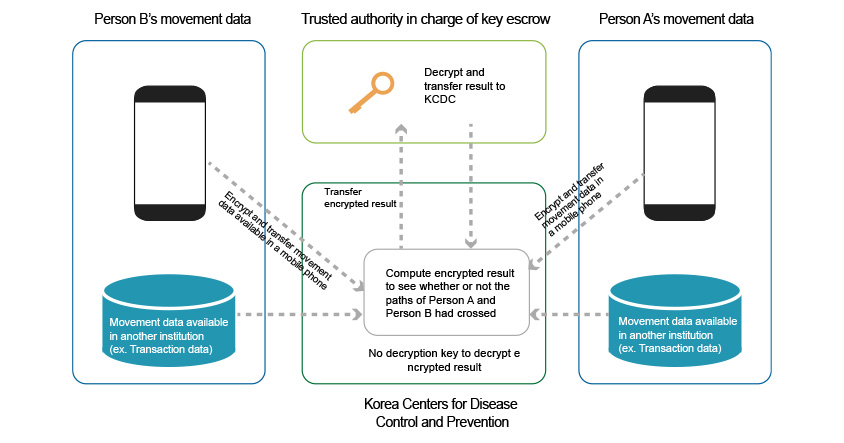 [Diagram 2] Decryption Key Operation Method
[Diagram 2] Decryption Key Operation Method
Conclusion
The future competitiveness of a nation as well as companies depends on how well it uses the data available. Although it is true that Korea, with recently amended ‘Three Data Laws’, has paved the way for greater use of data, issues concerning personal information misuse have also been raised as well. For that reason, we need to pay attention to personal information protection technologies including homomorphic encryption technology (enables enterprise and/or government organizations to share/utilize data whilst fully protecting personal information) as well as confidential computing, ZKP (Zero-Knowledge Proof) and DP (Differential Privacy) which were not introduced in this report.
▶ The contents are protected by copyrights laws and the copyrights are owned by the creator.
▶ Re-use or reproduction as well as commercial use of the contents without prior consent is strictly prohibited.
- #Homomorphic Encryption
- #privacy
- #data protection
- #security
- #corona
- #movements
- #KCDC
- #COVID-19
- #Post covid-19
Samsung SDS Security Research Center
JIhoon Cho
Dr. Cho is currently leading the Security Research Center in Samsung SDS, and worked as a mobile security architect in smart phone industry. He is holding a PhD in information security from Royal Holloway University of London, and a Master's degree in cryptography from University of Waterloo.
Hyojin Yoon
Dr. Yoon is leading the Security Algorithm Team in Samsung SDS and focusing on cryptography and privacy protection technology. She is holding a PhD in Cryptography and Mathematics from Seoul National University in Korea.
Eunkyung Kim
Dr. Kim is working at the Security Algorithm Team in Samsung SDS on efficient algorithms and secure key management for homomorphic encryption. She is holding a PhD in mathematics from Ewha Womans University in Korea.
-
[Technology Toolkit]
It is Important to Prevent Security Risks from Development Phase! Trust CAFA+ to Do the Job -
[Technology Toolkit]
In the Age of When Customer Data Must Be Treated as a King, PET Will Take on the Responsibility - Samsung SDS America showcases Nexsign at Finovate Spring 2018
- Bridging the gap between user experience and mobile security
- The importance of secure browsers in commercial banking
