The solution to cloud security, EAMS PAM
- 2022-09-30
- 작성자 Kwanghui Hong, Yoonjung Kwon



A credential, which is cryptographic personal information used to verify users, contains authentication information that authorizes access to important system resources, such as passwords, SSH keys, certificates, and API tokens. In particular, root permission credentials, which are hard-coded and stored in the source code or script in plaintext, are easily exposed to hackers because of GitHub or environment variables. We will look at EAMS PAM, Samsung SDS's server account management and access control solution, which protects privileged accounts with a one-time password (OTP).
* EAMS: Equipment Account/Access Management System / * PAM: Privileged Account/Access ManagementWhy is privileged account/access management (PAM) necessary?
How are you using credentials?
The credentials we use today are unmanaged and ubiquitous. They contain authentication information that authorizes access to important system resources, such as passwords, SSH keys, certificates, and API tokens. However, once the root permission credential is created, it is hard-coded and stored in the source code or script as plaintext without being changed because of its impact to the service. The credentials stored this way are easily exposed to hackers because of GitHub or environment variables. Even after an actual hack occurs, changing the credentials is very difficult. Although the credentials are added for each new service, variables (e.g., continuous service expansion and change of the person in charge) make it challenging to manage them properly. Furthermore, it is very difficult to predict possible failures without knowing which services use credentials. Due to the reasons mentioned above, we often find ourselves in a dilemma of not knowing whether to change the credentials.
What are credentials?
Credentials refer to “qualifications” or “identification.” They are usually used as information or certificate that users submit to verify their identity in the authentication process. They include ID, password, or certificate used for logging in. For example, ID and password you use for online services are part of the credentials.
The problems of static credentials
The idea to solve these problems is “central management of credentials.” Yet, we cannot rest assured that plaintext exposure will be 100% protected with the central management of credentials. This is because the accounts of the credentials can be leaked through the users or applications. Even if the password is changed periodically, hacking may occur during the period when the password is not changed. Moreover, because all applications use the same credentials, it is hard to figure out which client is causing the problem.
[Wait!] What are static credentials?
Static credentials are any user credentials that are rarely changed or do not change. The static credentials here include static values (e.g., user name, password, etc.). Such static credentials have low security and are easily exposed to hackers, which is a security threat. Therefore, security experts recommend dynamic credentials to reinforce security. For example, a dynamic one-time password (OTP) can be used to enhance security.
The solution to cloud security: PAM
Privileged account/access management (PAM) refers to “a method of minimizing security threats by granting the minimum required permissions to privileged accounts.”
Some examples of privileged accounts are the root of Linux and the administrator account of Windows.
A privileged account refers to accounts that have full control over resources and system settings, such as files, directories, and services, and can access important data.
[Wait!] What is privileged account/access management (PAM)?
PAM is an abbreviation for “privileged account/access management,” which refers to a system that safeguards and manages access permissions for accounts with special privileges within an organization. PAM is usually used to reinforce security over accounts with privileged access, such as administrators or system operators. PAM enables access control, monitoring, and logging of these privileged accounts and protects the system from security threats. For instance, financial institutions or government organizations use PAM solutions to control access and perform audits of privileged accounts for better security.
How to grant credentials to privileged accounts: Dynamic credentials and workflow-based authorization
Samsung SDS provides Equipment Account/Access Management System (EAMS) as a server account management and access control solution.
[Wait!] What is equipment account/access management system (EAMS)?
An EAMS refers to a system that manages accounts and access privileges for equipment used in organizations. This allows organizations to systematically manage their equipment and reinforce security. For example, public organizations can leverage their EAMS to manage accounts and access privileges of the computers and equipment provided as public goods. Furthermore, organizations can utilize an EAMS to regulate and oversee equipment access based on specific departments or roles.
EAMS PAM is a PAM-only product of EAMS and provides an authorization method based on dynamic credentials and workflow for the authorization of privileged accounts.
First, let’s take a look at dynamic credentials. Dynamic credentials provide a one-time password for each session and cannot be used after a certain period (TTL). Also, a unique password is provided for each session even for the same ID, so even if credentials are leaked, the exact point (session) where the attack occurred is immediately detected.
On the other hand, the workflow-based authorization method temporarily grants access to the privileged account automatically only when a task is received. Normally, a specific identity that is authenticated was granted access to a server-privileged account, requiring continuous management. With the workflow-based authorization method, however, the minimum authority of a “work unit” integrated with the workflow is granted, and the authority can be automatically retrieved at the end of work to provide the service securely while maintaining work efficiency.
Introduction to the EAMS PAM, the cloud security solution of Samsung SDS
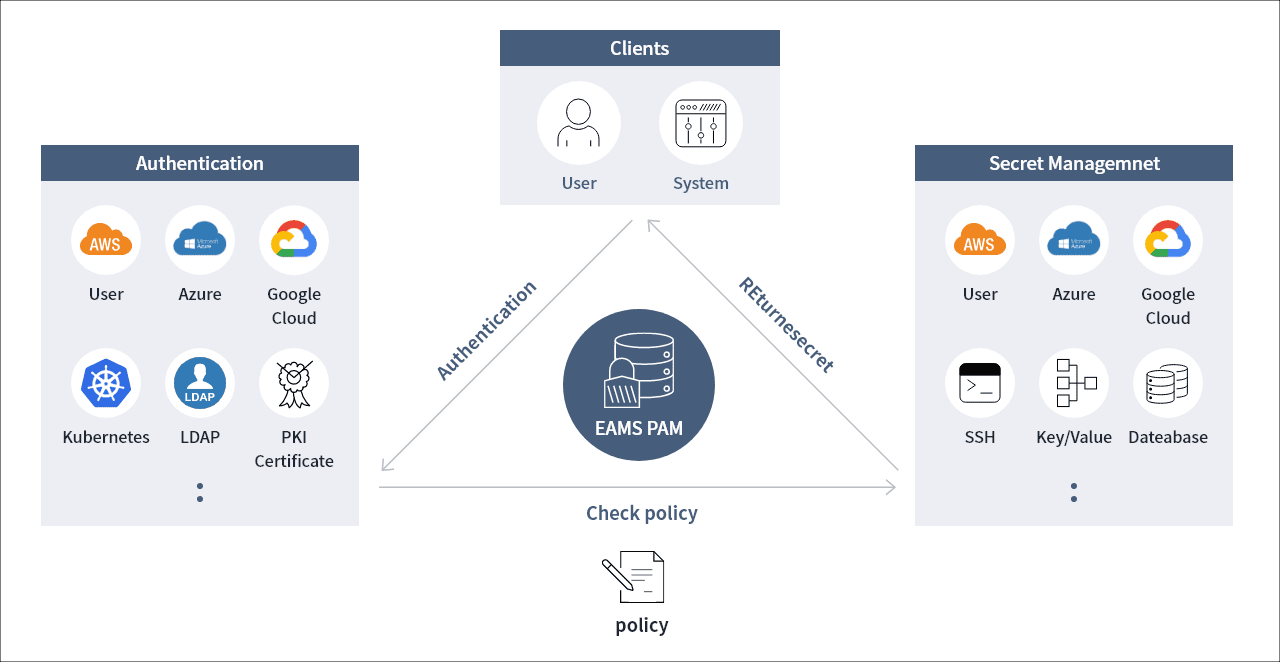
Providing PAM services requires a centrally managed solution for accounts. The Samsung SDS EAMS PAM solution protects privileged accounts by providing authenticated clients with a one-time password with minimal privileges according to the policy.
Feature 1) Dynamic credentials
EAMS PAM leverages technologies, such as Linux Pluggable Authentication Modules (PAM) and Windows AD, to provide OTPs to privileged accounts, including servers, DBs, and cloud VMs. Thus, even if the account information is exposed, the password cannot be reused. With the dynamic credentials, the password issued for each session will be different even with the same server, making it possible to detect the problematic session immediately.
Features 2) Various authentication methods
EAMS PAM provides various authentication methods, such as GitHub and LDAP, as well as Kubernetes, Token, and PKI certificates. Therefore, you can select an authentication method suitable for your client's authentication system. Automatic authorization for each user role is also possible by integrating with the authentication provider. Moreover, the authority is granted to the newly added users according to the group information once the accessible VM information is defined in advance according to the GitHub team and LDAP organization information. This approach manages not only users but also authentication processes for non-human entities like scripts and applications, ensuring that all entities utilizing privileged accounts can be properly identified.
Feature 3) Token-based permission management
EAMS PAM provides important credentials through permission management via tokens. Depending on the internal policy, clients (e.g., users, applications) are given a different server to show the password and validity period (TTL) for the password, respectively. Each client is issued a token after going through the authentication process in EAMS PAM, and each token has different policies applied.
With the token, the clients can access the server after requesting account information and issuing a password from EAMS PAM. EAMS PAM distributes tokens with permissions for each service so that privileged accounts are exposed only at essential points. Doing so protects the privileged accounts by centrally controlling which services consume important accounts and when.
- User
- System
- User
- Azure
- Google Cloud
- Kubernetes
- LDAP
- PKI Certificate
- User
- Azure
- Google Cloud
- SSH
- Key/Value
- DateAbase
The main features of the cloud PAM
The pain points of permission management in general cloud environments
In the general cloud environment, accessing multiple virtual machines (VMs) through a single key without a particular security setting was possible. Team members often share access keys for convenience, but this can cause a fatal security breach once the keys are exposed to attackers. As a solution, security standards can be applied to create individual IAM accounts for each user or separate accounts can be generated for each VM, allowing permissions to be granted on an individual basis. However, this can result in an additional workload. You need to manage and grant privileges to privileged VM accounts that are automatically created/deleted dynamically due to auto-scaling. To solve the problem, EAMS PAM provides an automated PAM service that can protect privileged accounts in a cloud environment.
Feature 1) Account management for cloud virtual machines through EAMS PAM
EAMS PAM is responsible for dynamically changing all VM accounts in the cloud and providing passwords to clients. The client refers to a user or privileged account-using system (i.e., script, application, etc.) that can request access or account information through EAMS PAM. In the past, even with the introduction of account management systems, there were cases where automated account management features couldn’t be effectively utilized due to the usage of service accounts in scripts or applications. Yet, with EAMS PAM, the passwords are provided to the service utilization account instead of the access account, allowing the distribution process of all privileged accounts to be visualized. With cloud VMs, it is hard to tell if privileged accounts are properly managed because they are dynamically created/deleted, but with EAMS PAM, you can check accounts with unchanged passwords, unused accounts, and accounts with illegal access from the account status dashboard.
Internal network
- User
- HTTPS
- EAMS PAM
HTTPS
-
VPC
Public Subnet EAMS Web Terminal
SSH/RDP
Public Subnet instances
-
VPC
Public Subnet EAMS Web Terminal
SSH/RDP
Public Subnet instances
Feature 2) Access management for cloud virtual machines through EAMS PAM
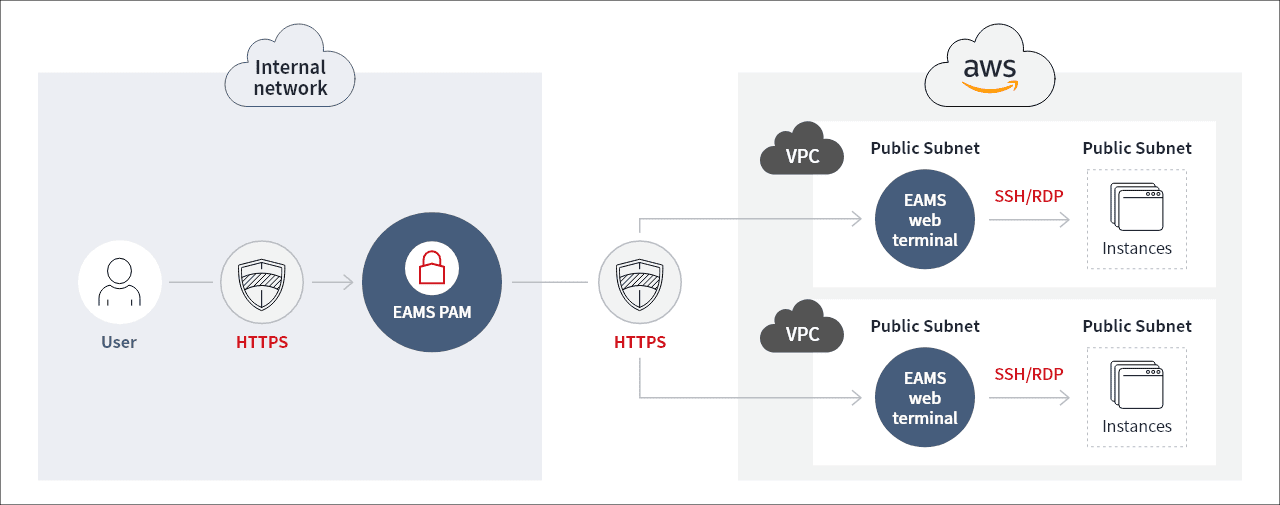
EAMS PAM provides a web-based terminal called "Privileged Access Manager" for single access to all VMs. Privileged Access Manager grants access to VMs without installing terminal programs for each protocol (e.g., SSH, RDP, Telnet, etc.) as long as a web browser is on the user's PC. Since it provides automatic login terminal access to all VMs, the VM account password is not exposed to users. In addition, installing another terminal program is unnecessary, so you can safely access it without managing security vulnerabilities. EAMS PAM maps out accessible VMs for each user and grants permission. In the case of privileged accounts, you can access them after getting administrator approval and automatic application of privileges by role will also be provided. For third-party users, including vendors and business partners, integration with the task management system allows temporary device access only during the duration of the assigned project.
Feature 3) Automatic deployment and safe connectivity in the cloud through EAMS PAM
EAMS PAM is easily installed in the cloud network since it can be downloaded from the marketplace and instantly configured. In the past, you had to open every SSH and RDP connection port of VM outside to access the VMs in the customer’s private network. But with EAMS PAM, only the HTTPS port is required to open, which makes the security management point simplified. Furthermore, security management scopes are reduced since only HTTPS protocol security vulnerabilities are managed without having to continuously control protocol security vulnerabilities, such as SSH, RDP, and Telnet.
Feature 4) Cloud virtual machine monitoring
Since both users and systems are based on the real name system, users can view and manage which and when VM privileged account was consumed by the account requesters. Also, you can prevent further security breaches with the dynamic secret method. The method detects and reports security threats when an authentication request is made to the VM more than once with the same password. On the other hand, with Privileged Access Manager, it is possible to audit text and video and trace who accessed which equipment and did what. The dashboard provides information about unauthorized access not facilitated through EAMS PAM, enabling you to trace the causes of security incidents resulting from unauthorized connections.
How to use EAMS PAM, a security solution for the cloud
Account management plan for cloud virtual machines
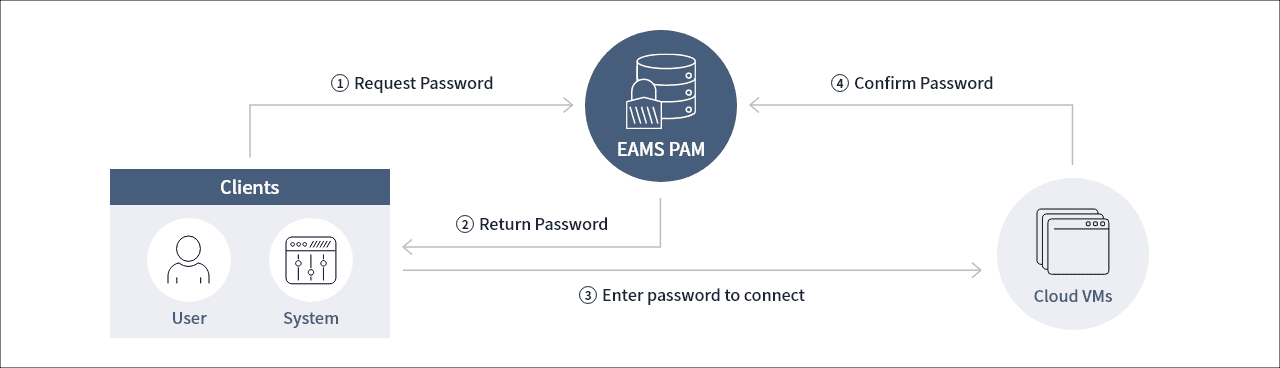
The following is a scenario of managing cloud virtual machine accounts via EAMS PAM. The dynamic credential method which provides one-time passwords for privileged accounts (i.e., Linux, Windows, and DB) is the basis of the PAM account management. The detailed sequence is as follows:
① A user accesses the EAMS PAM web and requests the VM password to access the VM.
② The user receives a one-time password for the VM from EAMS PAM.
③ When the user enters the password to access the VM,
④ The VM asks EAMS PAM to check if the password is valid and authenticates it. Once the server session is disconnected, the one-time password becomes invalid.
- 1. Clients access EAMS PAM and request passwords
- 2. EAMS PAM returns passwords to the clients
- 3. Clients enter passwords and access Cloud VMs
- 4. Cloud VMs verify the passwords through EAMS PAM
Privileged Access Manager, a web-based terminal of EAMS PAM, allows users to automatically access the server through the internal process without having to verify and enter a password in EAMS PAM separately. As a prerequisite to using the dynamic credential method, the agent should be installed on the Linux VM and enabled for Pluggable Authentication Modules (PAM) authentication. When setting PAM authentication, EAMS PAM is integrated as an authentication server. For Windows VMs, it must be integrated with AD.
However, if you cannot install the PAM agent on a Linux VM due to operational circumstances or if you have a Windows VM that is not connected to AD, the password will be provided with a static credential method, in which the password will be automatically changed at regular intervals (generally in every three months), instead of using a one-time password.
Workflow-based access plans for cloud virtual machines
The following is a scenario of providing business-based access via EAMS PAM. In the past, if third-party users, such as vendors and business partners, needed to access the VM, we issued VM privilege accounts for them. However, if the administrator does not check and reclaim the authorization after project termination, the threat of access to in-house resources will always be out there.
To deal with this problem, EAMS PAM provides access only to the designated VM during the assigned project period by integrating with project management systems, such as Jira and GitHub. When an administrator creates a user's project ticket in Jira or GitHub, permission to access the VM related to the project is automatically granted. When the user visits EAMS PAM, the list of authorization granted to the user will be displayed, and the user can access the VM via Privileged Access Manager provided upon connection. Since the Privileged Access Manager provides an auto-login terminal, the privileged account passwords are not exposed.
When the user ends the VM session after working, the job history and video are attached to the project management system. When the project is finished, the user will automatically be deleted from the VM access list, and it becomes impossible to connect to the VM afterwards. In this way, the administrator does not need to check and reclaim external members individually and the access rights are automatically granted and recovered for each project unit, enabling safer and more automated authority management.
DevSecOps plan in the cloud
The following is a scenario of securely managing privileged accounts in a DevOps framework through EAMS PAM. Recently, in the cloud native environment, the continuous build and deployment (CI/CD) method using DevOps system is becoming more common. However, there are cases in which privileged accounts are exposed, depending on the level of source code management and the security strength of the tools used on the DevOps Pipeline. To deal with the issue, EAMS PAM proposes a DevSecOps (DevOps + Security) use case that adds security to DevOps as a solution. In order to configure the DevSecOps system, it is necessary to manage essential credentials, such as DB connection information, in the application source code to be hard-coded and not exposed on the Internet. In particular, privileged accounts should be stored in a safe place so that they are not affected by the security level of tools used in the DevOps Pipeline (i.e., Jenkins and Ansible Tower).
On the other hand, in the cloud native environment, infrastructure as a code is created and managed. Also, when containers are deployed on the cloud VM and Kubernetes, detailed management is required to avoid cases where application configuration information, including privileged accounts, is stored in plaintext in the manifest file. EAMS PAM contributes to DevSecOps system establishment by centrally managing privileged accounts used in source code, DevOps Tool, VM/container deployment manifest, and API provision to support systems to consume accounts securely. With EAMS PAM, it is possible to use the real name through the system's own authentication process and to monitor when and what accounts the system used.
Closing Remarks: EAMS PAM, the solution to cloud security
So far, we have seen how EAMS PAM can protect privileged accounts in a cloud environment. We also looked at how to manage VM accounts and access via EAMS PAM and how to protect privileged accounts in a DevOps environment. In the increasingly complex and dynamically changing cloud environment, the solution provided by EAMS PAM for protecting critical resources and data is an excellent resolution to unpredictable cybersecurity threats.
- Kwanghui Hong / Samsung SDS
- Based on 20 years of development experience in the field of Home IoT solutions, office/IoT network service, and data center infrastructure remote access control solutions, Kwanghui Hong has experience in the Privileged Account/Access Management (PAM) field in the MSP environment.
- Yoonjung Kwon / Samsung SDS
- Based on the experience of developing an infrastructure operation automation solutions for domestic and overseas data center and cloud customers and planning Cloud PAM service, Yoonjung Kwon has expertise in cloud native technologies, such as containers and CI/CD.