
Keeping your sensitive information safeguarded gets harder every day, not only in your IT infrastructure, but also on mobile devices. Increasing cybersecurity challenges and stringent regulations such as the European NIS2 Directive for critical infrastructure and the upcoming Cyber Resilience Act require robust security measures to protect critical data and operational resilience.
As the majority (81%) of enterprises pledge to modernize their mobility management programs, many are turning to next-generation Enterprise Mobility Management (EMM) solutions, particularly given the rising cybersecurity challenges and stringent regulations like the European NIS2 directive for critical infrastructure and the upcoming Cyber Resilience Act. These regulations demand robust security measures to protect critical data and operational resilience.
Enterprises adopting EMM report significant benefits across their mobile device programs’ lifecycles: 88% report improved security, 90% enhanced productivity, and 91% freeing up business resources.
While 94% of enterprises state that they’re satisfied with their EMM solutions, not all are created equal. Moving from satisfactory to exceptional requires understanding the key considerations for choosing the optimal EMM solution in today’s rapidly evolving marketplace.
Key Considerations for Choosing an EMM Solution:
Comprehensive Technology Integration
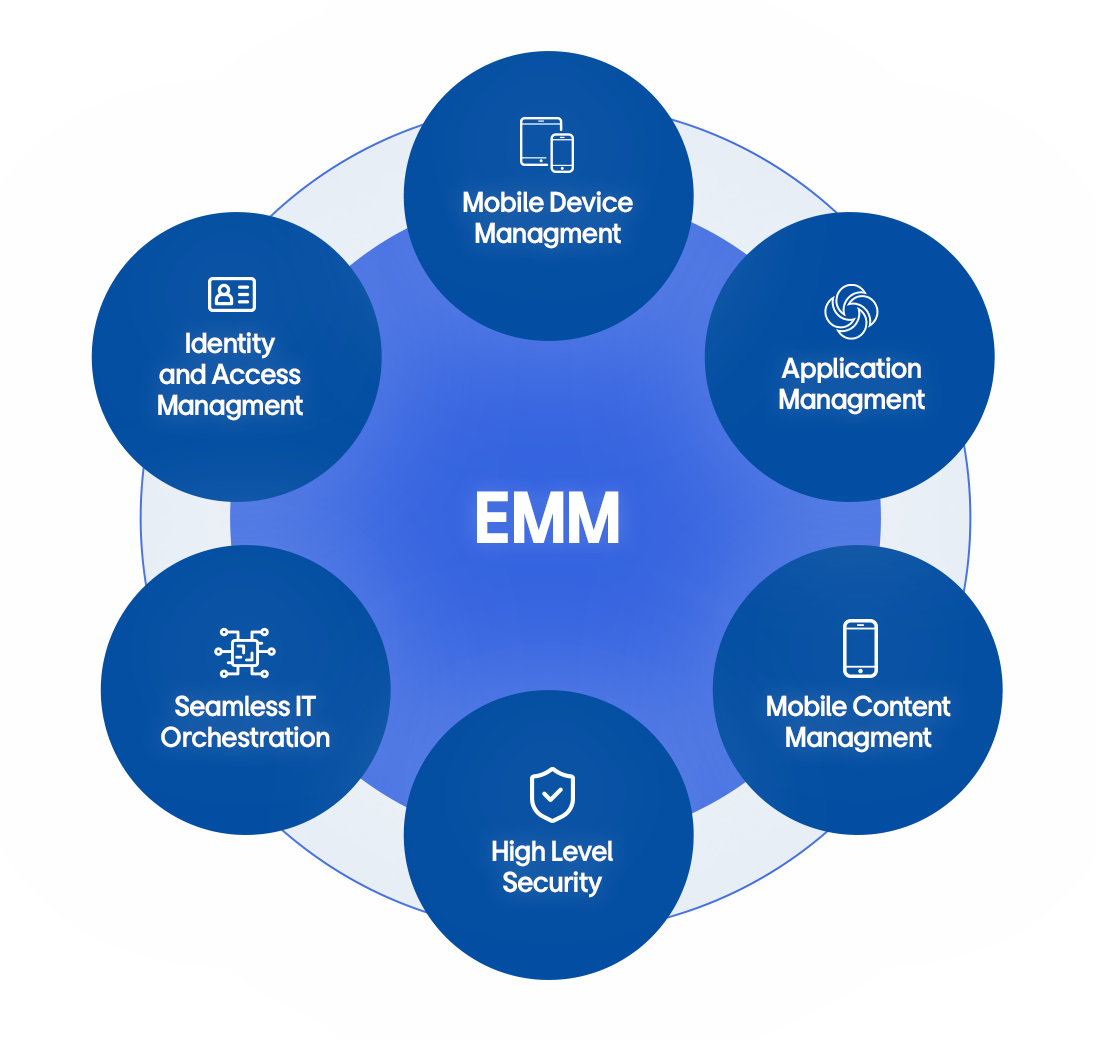
EMM solutions vary in functionality. Advanced solutions integrate the following six technologies into a unified platform:
- Mobile Device Management: Enables secure monitoring, managing, and supporting of all mobile devices used within the enterprise. IT administrators can enforce policies, configure settings, and ensure compliance on smartphones, tablets, and other devices.
- Application Management: Enables the deployment, updating, and secure management of applications. It supports both public app store apps and proprietary tools, ensuring app-level security and productivity.
- Mobile Content Management: Ensures secure access, distribution, and management of corporate content on mobile devices. By enforcing encryption and access control policies, it protects sensitive documents and media.
- High Level Security: Ensure the highest level of security with global security certifications such as CC, CSfC, and STIG even in an air gap network
- IT Orchestration: Seamlessly integrate and excel with third party solutions from on-boarding to secure communication, providing a precise management of mobile devices regardless of their OS or device type
- Identity and Access Management: Manages user identities and authentication methods for mobile devices. It integrates with identity systems to verify credentials and control access to corporate resources.
EMM
- Application Management
- Mobile Content Managment
- High Level Security
- Seamless IT Orchestration
- Identity and Access Managment
- Mobile Device Managment
Security and Compliance
Security is a top priority for EMM solutions. Look for features that enable granular control over security settings, such as:
- Configuring detailed device encryption and enforcing password complexities.`
- Managing application whitelists and blacklists.
- Enabling remote wipe, password resets, and Wi-Fi configuration across devices.
Additionally, ensure that the EMM solution complies with key certifications like GDPR, FIPS 140-2, and NIAP Common Criteria. These standards are critical for regulatory compliance and safeguarding enterprise data.
Regulatory Frameworks: GDPR and NIS2
For organizations operating in Europe, compliance with the General Data Protection Regulation (GDPR) is non-negotiable. EMM solutions must facilitate data protection, user consent management, and robust reporting to meet GDPR standards.
Similarly, the NIS2 directive focuses on enhancing cybersecurity across essential sectors. EMM solutions should provide robust protection against cyber threats, aligning with the directive’s requirements to safeguard critical infrastructure.
Deployment Options: On-Premise vs. Cloud
Enterprises can choose between on-premise or cloud-based EMM solutions, depending on their specific needs:
- On-Premise: Ideal for organizations requiring complete control over data and infrastructure. Suitable for industries with strict compliance requirements.
- Cloud: Offers scalability, cost-efficiency, and ease of deployment. Suitable for dynamic, distributed workforces.
Cybersecurity Features
A strong EMM solution integrates advanced cybersecurity features to protect devices and data from evolving threats. Look for capabilities such as real-time threat monitoring, automated compliance alerts, and robust encryption methods.
Difference Between MDM and EMM
Since MDM solutions only work at the device level and focuses primarily on the administration of mobile devices by assigning policies and configurations to ensure their security and proper management. Therefore, it is difficult to overcome challenges from trends such as BYOD (Bring Your Own Devices) and COPE (Corporate Owned Personally Enabled) that have emerged in organisations. EMM provides a comprehensive solution, managing all aspects of mobile devices, including data, apps and access, to protect critical business data.
![[MDM vs EMM] image](https://image.samsungsds.com/eu/insights/250121_insight_eu_img_02.png?queryString=20250410013411)
EMM
- Configurations
- App management
- Email Management
- Security Management
MDM
- Device
- Management
EMM for High-Security Environments
Organizations operating in highly secure environments, such as those adhering to the Commercial Solutions for Classified (CSfC) program, require additional layers of protection. Key requirements include:
- Dual encryption for data in transit and at rest.
- Restricting unauthorized application installations.
- Operating in Cryptographic Module Validation Program (CMVP) mode.
These features ensure secure communication and compliance with stringent regulations, safeguarding sensitive information throughout the device lifecycle.
Conclusion
Choosing the best EMM solution requires careful evaluation of technology integration, security, compliance, and deployment options. By addressing these considerations and aligning with frameworks like GDPR and NIS2, enterprises can empower their workforce while maintaining robust cybersecurity.

Our Enterprise Mobile Management (EMM) is a comprehensive solution designed to protect your critical business data while managing mobile devices, making it indispensable for companies aiming to enhance employee mobility and productivity. EMM enables your organization to enforce strict security policies, ensuring sensitive business data remains protected. It allows secure delivery of corporate data by distributing content to authorized devices while restricting access for unauthorized users.
Centralized user and device management automates onboarding, assigns corporate resources and security protocols and streamlines device reassignment to employees. With a single console, EMM empowers IT administrators to set up, deploy, locate, protect and manage devices anywhere, ensuring seamless and secure device management across the organization.
Our on-premise EMM is ideal for enterprises and governments that require the highest level of security, which we ensure with global security certifications such as CC, CSfC and STIG.
Find out more about the many benefits of our Enterprise Mobility Management offering.
Contact our Experts >
Visit our EMM product page >

- Knox Native & E-Fota: Powerful extensions for your Enterprise Mobility Management
- Digital Government Innovation, Preparing for Hyperscale AI and Cloud
- How to automate factory and warehouse intralogistics to improve efficiency and productivity.
- INTRODUCINGDIGITAL MARKETING SERVICES
- Interview with Moritz: Enterprise Mobility Management [On-Premise]
