Config Inspection
Diagnosing Security Settings Vulnerabilities in the Cloud Console
Config Inspection is a service that diagnoses security settings vulnerabilities such as account management, resource and network diagnostics, monitoring and logging within the console to maintain a secure cloud environment. Using a security diagnostic checklist tailored for SCP, Config Inspection assesses the security settings of the product and posts its findings on the report. A guideline provides information on how to improve each vulnerability type and any potential failure and security risk can be addressed by taking preemptive measures against vulnerabilities.
Overview


-
Diagnosis Checklist by Domain and Service
Using cloud security best practices proposed by Samsung Cloud Platform, users can assess and manage security status of the console. Through the best practice analysis, various types of cloud security vulnerabilities can be identified with respect to IAM, authentication key management and network settings.
-
Easy-to-access Analysis Results
A report is provided to make it simple to check the analysis result by user requests. An analysis result provides details of the checklist, including diagnostic criteria and action guides.
01
04
Service Architecture
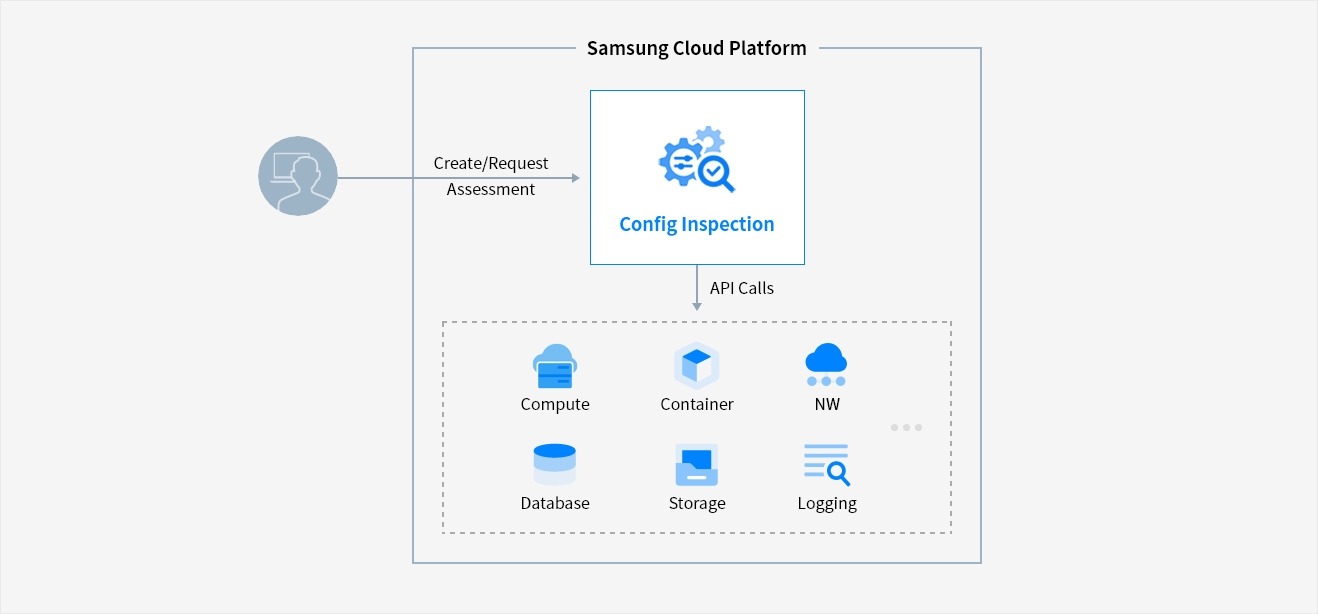
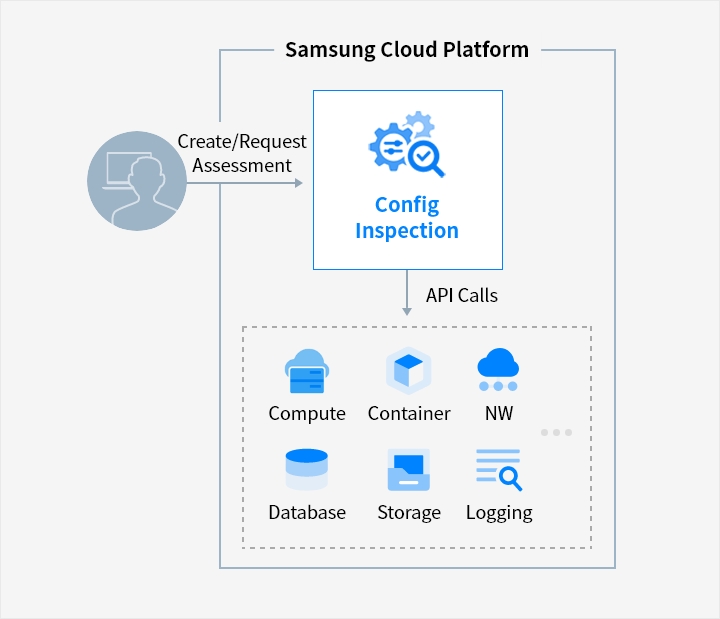
Samsung Cloud Platform
User → Create/Request Assessment → Config Inspection → API Calls → Compute, Container, NW, Database, Storage, Logging
Key Features
-
Diagnostic target management
- Diagnostic target : Account
- Checklist : Best practice
※ Best practice : Required security settings guide for Samsung Cloud Platform
-
Viewing a diagnostic result
- Viewing a diagnostic history(completed/failed)
- Providing details including checklist item-diagnostic criteria, action guides, etc.


Let’s talk
Whether you’re looking for a specific business solution or just need some questions answered, we’re here to help